
SUMMARY
Web server security is an ongoing process rather than a final state. Key to this process is an understanding of existing vulnerabilities. Therefore, these vulnerabilities must be actively sought out with the same zeal as the attackers. Like malicious hackers, we will use a wide array of technical methods to analyze the attack surface of the target site. These technical methods will include network mapping, SQL injection, password attacks, and web application scanning. Additionally, social engineering attacks will be considered. These will include social media tracking and the use of online personal information databases directed against management and executives.
TOOLS
Kali Linux
The Kali Linux distribution is the operating system of choice for security and penetration testing. It comes with more than 600 tools preinstalled yet is compact enough to run from a bootable USB drive. This means that whether the testing is from an internal network location or external, or even mobile, Kali Linux is a great tool.
Wireshark
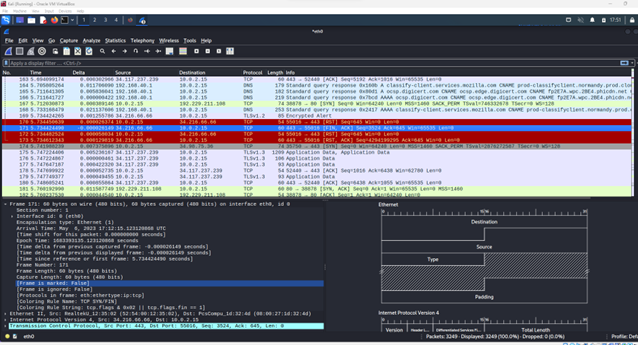
Wireshark is a network protocol analyzer. It monitors network interfaces and can examine packets down to the level of individual bits. All this information is necessary for traffic analysis and for acquiring password hashes and the like as they are transmitted across the network.
Aircrack-NG
Aircrack-ng is a wireless network protocol analyzer, serving many of the same functions as Wireshark. Additionally, aircrack-ng has integrated tools for faking a wireless access point, packet injection, and password cracking. Fake wireless access points are used to get users to connect and transmit data allowing for a great deal of information to be captured.
Nmap
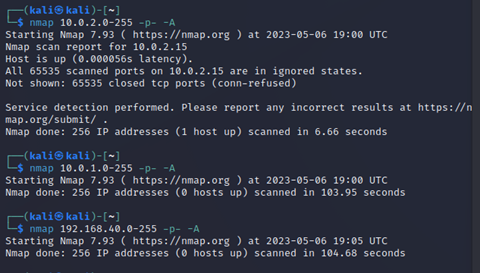
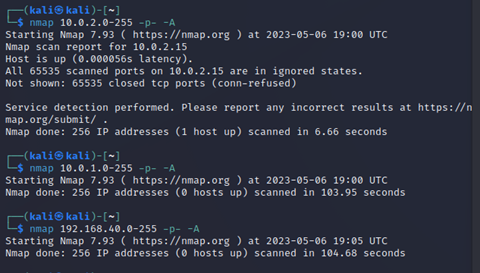
Nmap is a network mapping tool. It detects hosts on the network and all the ports on those networks, revealing potential points of access and attack.
OWASP Zed Attack Proxy

Zed Attack Proxy (or “ZAP”) is maintained by the Open Worldwide Application Security Project and can be used to scan HTTPS activity in a passive mode or to actively attack using known vulnerabilities. ZAP then can be used to generate reports of vulnerabilities found, as pictured above.
Wappalyzer
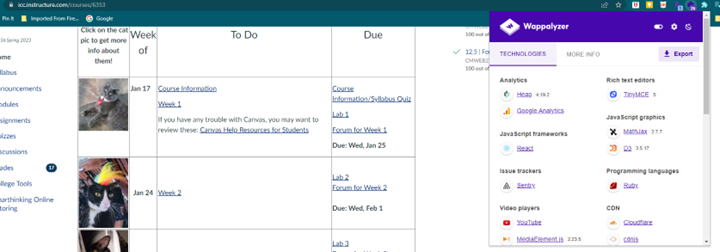
Wappalyzer is a browser extension that analyzes which web applications and technologies are in use on a website. This knowledge is very important for attackers because every application has its own suite of vulnerabilities that the attacker can exploit.
Hashcat
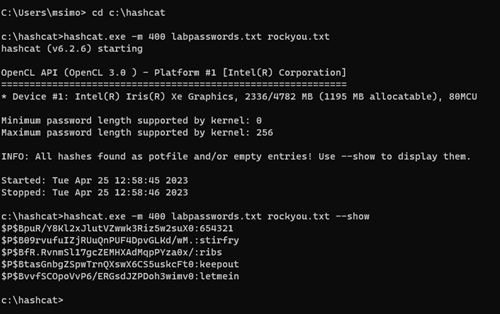
Hashcat is used after Wireshark and Aircrack-ng captured packets containing hashed passwords to extract those passwords. Similar products, such as John the Ripper, Hashsuite, and Cain and Abel, may also be used for password cracking.
SQLMap
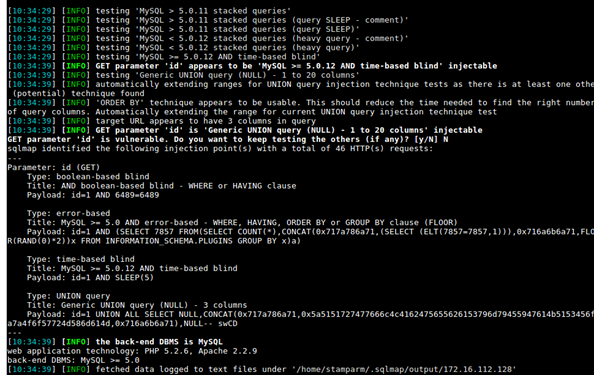
SQLMap is designed to attack SQL databases. It can perform SQL injections and attack database passwords. Once it has successfully accessed the database it can be used to execute any command or even dump the entire database.
Google Dorks
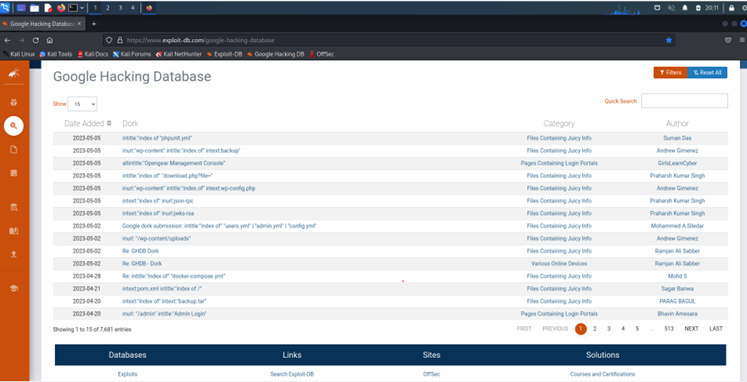
Google Dorks are a collection of known scripts that attack various server and application setups. They represent the low hanging fruit of attacks, but still must be protected against. Searching the Google Hacking Database for relevant vulnerabilities will allow them to be closed.
Radaris People Search
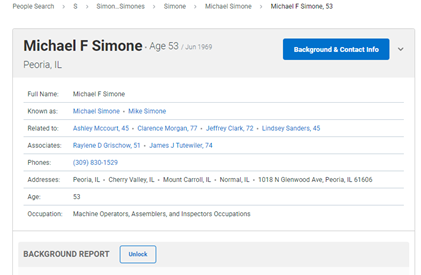
Radaris People Search is a tool for learning as much as possible about the employees, management, and executives of a targeted company. It gives a great deal of detail on the person, but also on their relationships to other people.
Social Media
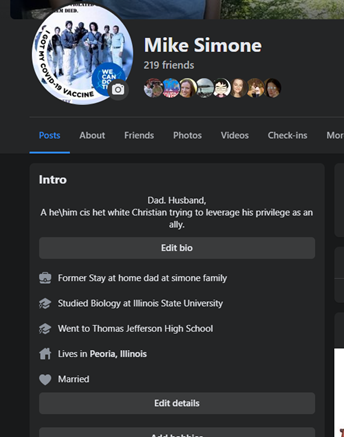
The social media of the target institution, its employees, and partners is an excellent source for information. It gives possible usernames, password sources, busy and slow times of work, even times when important staff may be on vacation.
TECHNIQUES
Overview
There are five penetration testing phases: reconnaissance, scanning, vulnerability assessment, exploitation, and reporting. Different tools are used, or the same tools are used differently, for each step. The steps flow into each other rather than have sharp divisions.
Reconnaissance
This step is focused on gathering information about the target. Social media monitoring and public databases are used here to learn as much about the human side of the target system as possible. This information can then be used to identify possible targets for spear phishing and other social engineering attacks, or even as sources for possible usernames and passwords. Technical reconnaissance begins with whois lookups and examination of other public facing data such as DNS and mail servers. Wappalyzer is also used now to discover the technologies used on external web servers. All these actions are directed at getting the best picture of the target for planning the later phases with the lowest chance of alerting them.
Scanning
This is the more active and in-depth follow-on to the reconnaissance stage. Nmap is used to locate targets by their IP address and to determine which ports they have open. Wireshark and aircrack-ng are used to monitor the network and record activity that is significant, especially anything that appears to be a password hash. Zed Attack Proxy is used in passive mode to scan HTTPS traffic and determine what applications (including version numbers and updates) are in use. Metasploit Framework can also be used as a scanner to learn what apps are present and running over the network. The information gathered here is used to steer the vulnerability stage towards the proper attack vectors to investigate.
Vulnerability Assessment
This phase is about determining what vulnerabilities are present on the targeted network. Metasploit Framework and Zed Attack Proxy are used in their active modes to determine specifically which vulnerabilities are present. Hashcat and other password crackers are used on any captured hashes. The Google Dorks database can be searched for any relevant attacks and used to probe the target. Spear phishing attacks can be launched at the most likely victims. A comprehensive list of all detected vulnerabilities must be kept for presentation to the client for remediation. Once this list of vulnerabilities is complete, the attacks can begin to exploit them.
Exploitation
The exploitation phase is about attacking the detected vulnerabilities. Here the Metasploit Framework is used to deliver active payloads and Google Dorks are triggered. SQLMap and similar tools are used to make SQL injection attacks. Spear phishing payloads that were successfully delivered can be used to escalate privileges in the system. The specific attacks and their effects must be fully documented, with any damage to a production system being purely cosmetic and easily fixed. If the target was purely a demonstration system, the damage can be more extensive to give the client a better idea of what can be done to unprotected systems.
Reporting
The final stage is reporting. In reporting, the penetration testers must give a detailed accounting of the steps they took, what worked, what didn’t work and their clean-up. Additionally, the penetration testers should explain how to rectify the problems that were discovered. This stage can be considered the most important, as it is the culmination of the work put in during all the other stages.

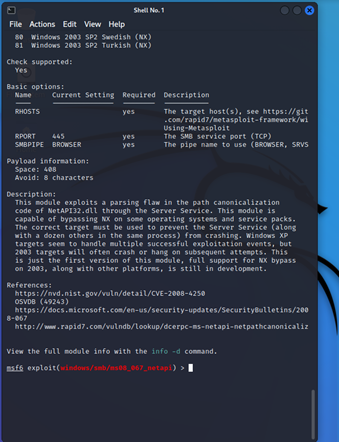










Social Media
The social media of the target institution, its employees, and partners is an excellent source for information. It gives possible usernames, password sources, busy and slow times of work, even times when important staff may be on vacation.